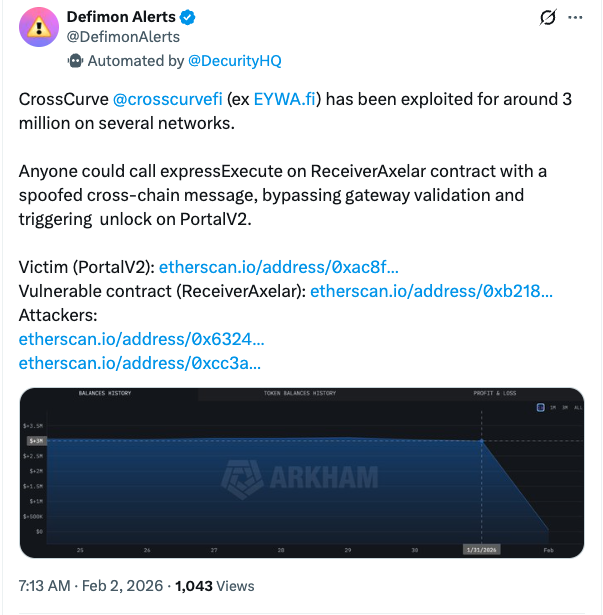
In the US, **A major crypto scandal has emerged that includes John Daghita (known online as “Lick”) in the alleged theft of more than $40 million from government seizure addresses. ** **
Daghita’s father, who runs CMDSS, is a Virginia-based IT company that has signed ‘2024 deal to help the US Marshals Service (USMS) manage and dispose of stolen and lost crypto assets.
Alleged Insider Access Enables Massive Government Crypto Theft
The theft was reportedly facilitated by Daghita’s access to private crypto addresses through his father’s position at CMDSS.
Blockchain investigator ZachXBT has reportedly traced at least $23 million to one wallet while the exact mechanics are still unclear. It directly links the wallet to suspected thefts totaling over $90 million, from 2024 to late 2025.
X (Twitter) and LinkedIn accounts were deleted by CMDSS in response to the growing scandal. They also removed its employee and team information website from its site.
Update: The CMDSS company X account, website, & LinkedIn were all just deactivated pic.twitter.com/nvN6u5XMPq
ZachXBT (@zachxbt) January 25, 2026
ZZXBT noted that Daghita remained active on Telegram with assets associated with the theft and even using public addresses linked to the investigation.
Read the threat actor John (Lick) > 1/ Meet the threats, who was caught in a wallet address directly tied to $90M+ in suspected thefts from the US Government in 2024 and several other unidentified victims between Nov 225 and Dec 2025. Pic pic. tweeted @? SBAFU5hTnE com/SBAFA5Htne
ZachXBT (@zachxbt) January 23, 2026
But Daghita quickly removed NFT usernames from his Telegram account, reportedly changing the user’s screen name after the post, complicating attempts to track down the stolen money.
Government Contracts and Insider Risks Highlighted by the Daghita Case
In government IT contracting, CMDSS is not a minor player. Throughout the years, the firm has maintained active contracts with both the Department of Defense and the department of Justice. Adding to concerns over the level of sensitive data/materials that Daghita may have access before the scandal emerged, this raises questions about how much information or assets might have been available.
Analysts are calling for urgent audits and transparency to assess the full scope of potential losses.
Another massive crypto scandal is coming to light, this time involving a man named John Daghita.
In Virginia, CMDSS is a company owned by > John’s father and has been named for the name of his business. U.S. – Under the Biden administration in October 2024, . S S. Government signed a large deal with the firm to help the.
Jacob King (@JacobKinge) January 25, 2026
This incident highlights a recurring vulnerability in crypto custody arrangements, even within government-sanctioned frameworks.
Even with sophisticated oversight, human connections and insider access can pose significant risks.
Investigators remain investigating both the technical and organisational aspects of the alleged theft. The CMDSS’s operational protocols are being investigated by authorities and the extent to which the firm’s government contracts may have inadvertently provided access to valuable crypto assets.
John Daghita’s alleged theft represents one of the most high-profile breaches of government-managed crypto assets in recent memory.
Thanks for reading $40 Million Crypto Heist Allegedly Linked to US Government Contractor’s Son