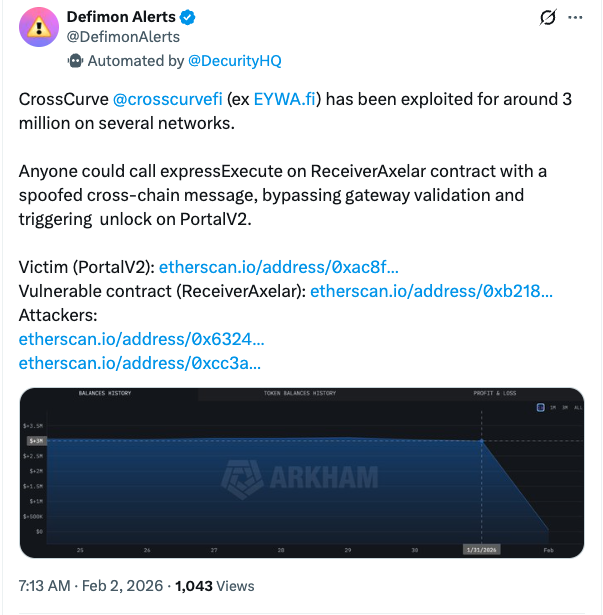
The offline computation protocol Truebit’s $26 million exploit is the result of an attacker’ patented contract flaw that allowed for minting tokens at near-zero cost, which highlights persistent security risks even in long-running blockchain projects.
Truebit was hacked for $26 million and the truebit (TRU) token crashed 99%, Cointelegraph reported Friday.
A loophole in the protocol’s smart contract logic allowed attackers to mint “massive amounts of tokens without paying any ETH” according to blockchain security company SlowMist, who published a post-mortem analysis Tuesday.
Due to a lack of overflow protection in an integer addition operation, the Purchase contract of Truebit Protocol produced something wrong when it was calculated how much ETH needed to mint TRU tokens, SlowMist said.
A “sale” of the smart contract’s price calculations were then “erroneously reduced to zero”, meaning that the attacker could drain the contract’s reserves by minted $26 million worth of tokens “at nearly no cost” according to the post mortem.
since the contract was compiled with Solidity 0. 6 s. Unlike in the previous version, overflow checks were not included in these calculations (calculations exceeded the maximum value of “uint256” to produce an ‘ailent over flow’ and thus resulted in a “wrap approximately small value near zero”. Paraphrasingr ’It is.
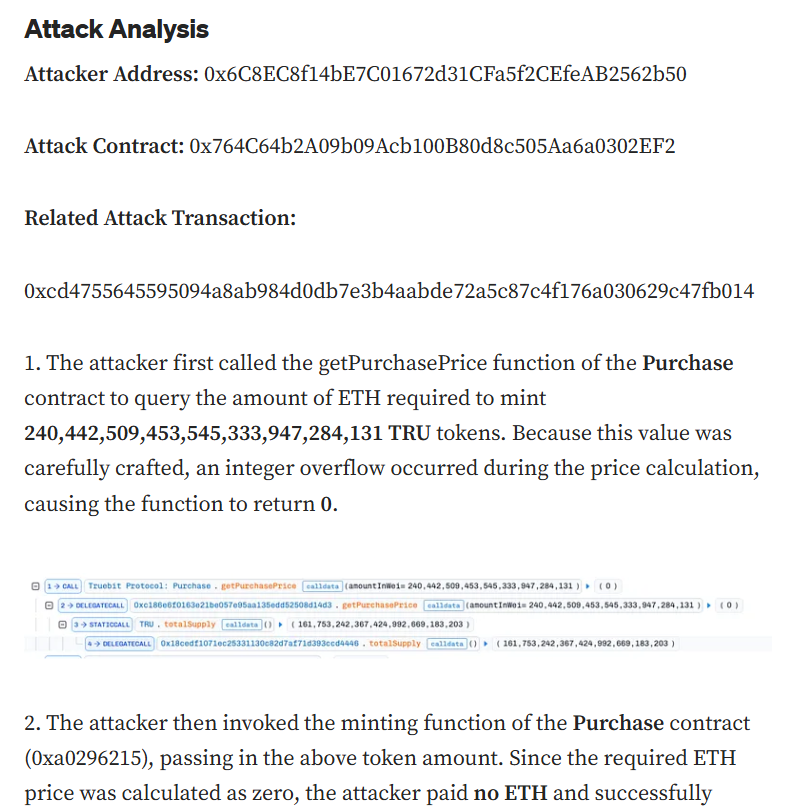
Truebit exploit post-mortem analysis. Source: SlowMist
Related: Fake MetaMask 2FA security checks lure users into sharing recovery phrases
According to the exploit, even the more established protocols are hacked by hackers. It was almost five years ago that Truebit was launched on the Ethereum mainnet, nearly five decades after it had been released in April 2021.
In late last year, interest was sparked by smart contract security after an Anthropic study revealed that commercially available artificial intelligence (AI) agents had found $4. 6 million of smart contract exploits from a worth 6m.
Claude Opus 4 of Anthropic is an anti-phraser. Claude Sonnet 4 ( 5),. The exploits were collectively developed by 5 and OpenAI’s GPT-5, a group of $4-million worth of exploiting. A research paper released by the AI company’s red team, which focuses on finding code vulnerabilities before malicious actors, found 6 million when tested on smart contracts.
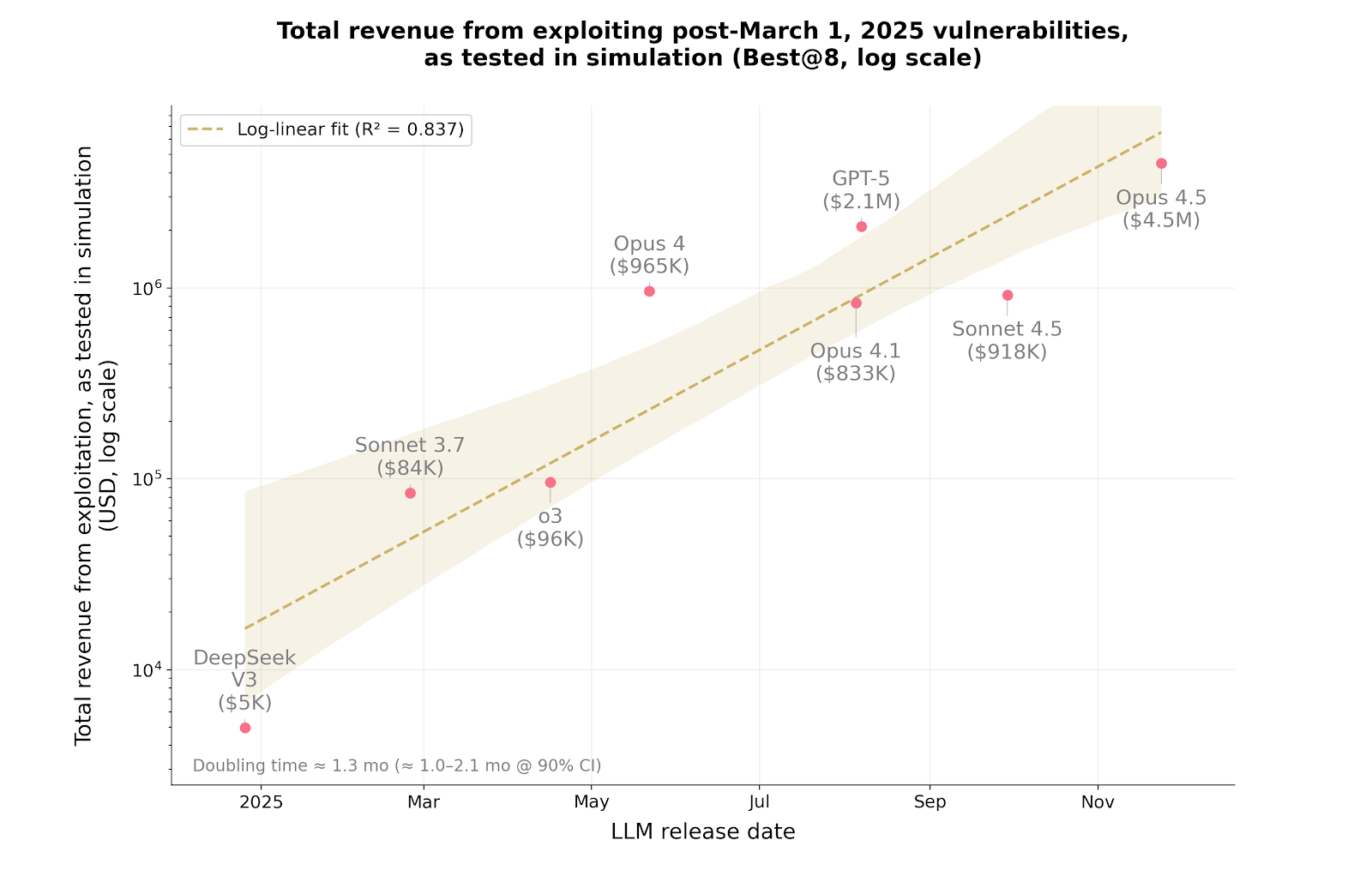
Chart of AI exploiting revenue from simulations. Source: Anthropic
Related: Bitcoin investor loses retirement fund in AI-fueled romance scam
Smart contract bugs largest attack vector of 2025
In 2025, the largest attack vector for the cryptocurrency industry was smart contract vulnerabilities (56 cybersecurity incidents), and account compromises were second with 50 incidents – according to SlowMist’s year-end report.
A total of 30 contract vulnerabilities were. In 2025, 5% of all the crypto exploits were made by parodyr; 24% for hacked X accounts and 88% private key leaks. 5% in third place, while .
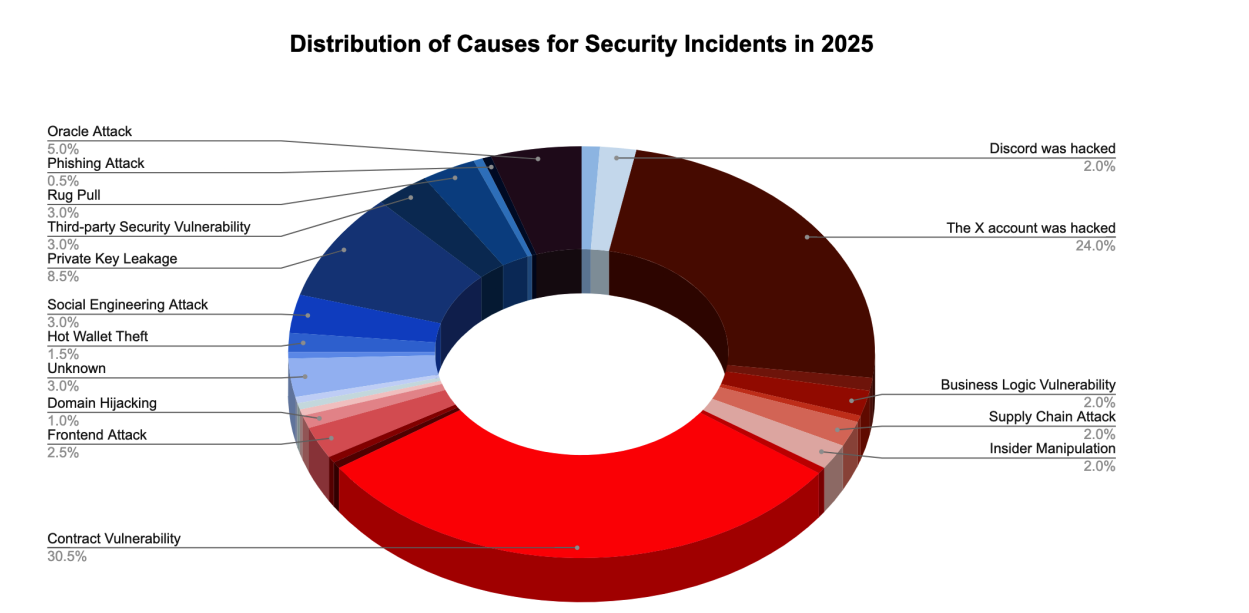
Distribution of causes for security incidents in 2025. Source: SlowMist
Meanwhile, other hackers are switching strategies from protocol hacks to exploiting weak links in onchain human behavior.
Blockchain security platform CertiK reported that crypto phishing scams were the second-largest threat of 2025, costing crypto investors a total of $722 million over 248 incidents.
Phishing attacks are social engineering schemes that do not require hacking code, such as crypto phishing. A attackers instead use a scam-based link to steal victims’ sensitive information, including the private keys to crypto wallets and other personal data.
Investors are now heeding this threat, however, as the $722 million is 38% less than $1 billion stolen through phishing scams in 2024.
Magazine: Meet the onchain crypto detectives fighting crime better than the cops
Thanks for reading Truebit exploit exposes smart contract flaw behind $26M token mint